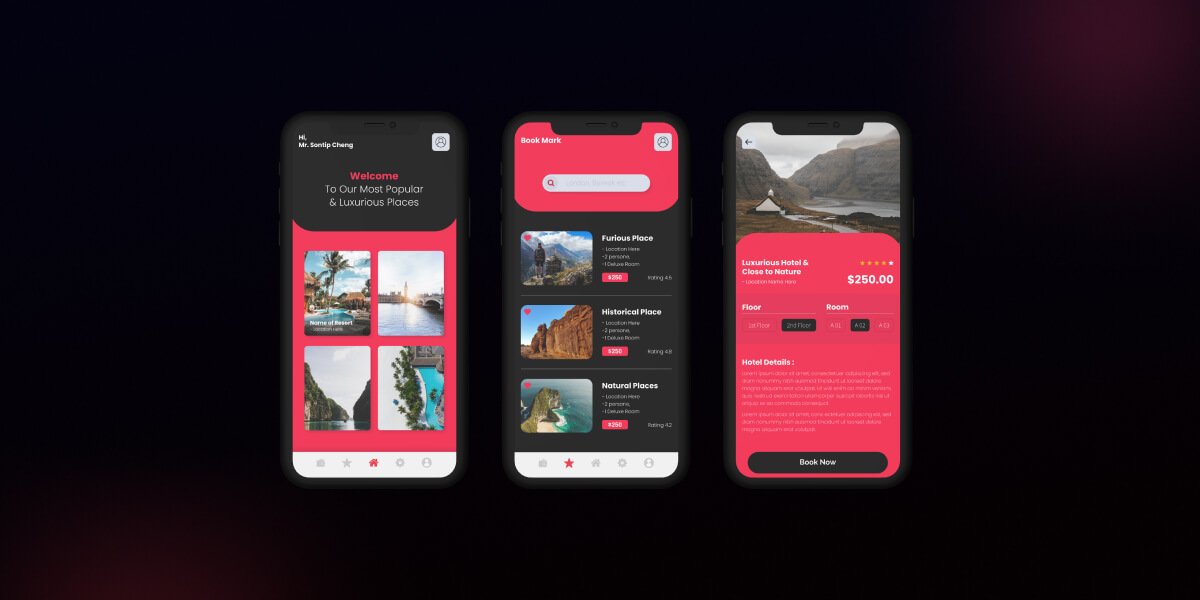
NFT Dashboard Application Development.
Through a wide variety of mobile applications, we’ve developed a unique visual system.
- Client George Wallace
- Date 15 June 2022
- Services Web Application
- Budget $100000+

A proven expert in B2B Sales, Account Management, and Consulting, this professional consistently meets and exceeds sales goals by demonstrating a deep understanding of market dynamics and client needs, not only have sales targets been surpassed, but client relationships have also been expertly nurtured and managed. The ability to craft customized solutions that resonate with customers underscores their expertise. Success in sales, account management, and consulting is highlighted by a strategic approach that combines market insight with outstanding customer engagement.



















(Secure Access Service Edge)*: A cloud architecture model that combines networking and security functions with WAN capabilities to support dynamic secure access to organizational resources.

(Security Service Edge)*: Part of the SASE framework, focusing specifically on security services that are delivered at the edge of the network to provide safe cloud access to applications and data.
VoIP (Voice over Internet Protocol)*: A technology that allows voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the internet.

UCaaS (Unified Communications as a Service)*: A service model where a provider delivers a variety of communication and collaboration applications and services, typically over the internet, as a unified package that can include voice, video, messaging, and collaboration capabilities.
MPLS (Multiprotocol Label Switching)*: A type of data-carrying technique for high-performance telecommunications networks that directs data from one network node to the next based on short path labels rather than long network addresses.

Dynamic IP*: An IP address that changes each time you connect to the internet, as opposed to a static IP which remains the same.

IT Managed Services*: Services where an external provider manages and assumes responsibility for a defined set of IT services for a client, typically on a proactive basis and under a subscription model.

TDM Replacement*: The process of upgrading from Time Division Multiplexing (TDM), an older technology used to transmit multiple signals over a single transmission medium, to more modern technologies like IP-based systems.
PRI (Primary Rate Interface)*: A telecommunications interface standard used on an ISDN (Integrated Services Digital Network) for carrying multiple DS0 voice and data transmissions between a network and a user.
Ethernet*: A family of computer networking technologies commonly used in local area networks (LAN), metropolitan area networks (MAN) and wide area networks (WAN).

Broadband*: A wide bandwidth data transmission with an ability to simultaneously transport multiple signals and traffic types. The medium can be coaxial cable, optical fiber, radio, or twisted pair.

LAN-WAN (Local Area Network - Wide Area Network)*: LAN refers to a network that connects computers within a limited area such as a residence, school, or office building, while WAN spans a larger geographic area such as cities, states, or countries.

Wireless*: Networking technology that uses radio waves to provide wireless high-speed internet and network connections.

Data Center*: A facility used to house computer systems and associated components, such as telecommunications and storage systems. It generally includes redundant or backup power supplies, redundant data communications connections, environmental controls, and security devices.

SIP Trunking (Session Initiation Protocol Trunking)*: A method of sending voice and other unified communications services over the internet. It works with an IP-enabled PBX (private branch exchange).

Hosted Services*: Services that are provided over the internet or through a dedicated cloud network where infrastructure and platforms are managed by an external organization.

Services that provide insights about the existing and emerging threats targeting various sectors, allowing organizations to proactively defend against malicious attacks.

These services help identify vulnerabilities in an organization's network and systems and simulate hacker attacks to test defenses, respectively.

A service that provides organizations with threat detection, incident response, and continuous monitoring capabilities, often using advanced analytics and human expertise.

Services that help ensure that only authorized and authenticated users are able to access the resources they need, and at the right time, enhancing security by managing user identities and permissions.

Outsourced services to manage and monitor firewall infrastructure which includes setup, configuration, maintenance, and upgrades to protect against unauthorized access.

Services that monitor network and/or system activities for malicious activities or policy violations and can react to block or prevent those activities.

Solutions that provide real-time analysis of security alerts generated by applications and network hardware. They help in the detection, analysis, and response to security incidents.

Services that encrypt data at rest, in transit, or in use to protect sensitive information from unauthorized access.

Services that protect endpoints such as desktops, laptops, and mobile devices from cyber threats, often including antivirus, anti-malware, and more sophisticated responses to emerging threats.

Services that protect data, applications, and infrastructure involved in cloud computing. These include solutions that address security governance, compliance, and risk management in cloud environments.

Services aimed at educating employees about the various aspects of cybersecurity, common threats, and best practices to mitigate risks.

Specialized services that help organizations prepare for, respond to, and recover from cybersecurity breaches or incidents.

Services that ensure an organization meets specific security standards and regulatory requirements, often involving comprehensive evaluations and recommendations for improvement.
Through a wide variety of mobile applications, we’ve developed a unique visual system.
There are always some stocks, which illusively scale lofty heights in a given time period. However, the good show doesn’t last for these overblown toxic stocks as their current price is not justified by their fundamental strength.
A strategy is a general plan to achieve one or more long-term. labore et dolore magna aliqua.
UI/UX Design, Art Direction, A design is a plan or specification for art. which illusively scale lofty heights.
User experience (UX) design is the process design teams use to create products that provide.
Toxic companies are usually characterized by huge debt loads and are vulnerable to external shocks. Accurately identifying such bloated stocks and getting rid of them at the right time can protect your portfolio.
Overpricing of these toxic stocks can be attributed to either an irrational enthusiasm surrounding them or some serious fundamental drawbacks. If you own such bubble stocks for an inordinate period of time, you are bound to see a massive erosion of wealth.
However, if you can precisely spot such toxic stocks, you may gain by resorting to an investing strategy called short selling. This strategy allows one to sell a stock first and then buy it when the price falls.
While short selling excels in bear markets, it typically loses money in bull markets.
So, just like identifying stocks with growth potential, pinpointing toxic stocks and offloading them at the right time is crucial to guard one’s portfolio from big losses or make profits by short selling them. Heska Corporation HSKA, Tandem Diabetes Care, Inc. TNDM, Credit Suisse Group CS,Zalando SE ZLNDY and Las Vegas Sands LVS are a few such toxic stocks.Screening Criteria
Here is a winning strategy that will help you to identify overhyped toxic stocks:
Most recent Debt/Equity Ratio greater than the median industry average: High debt/equity ratio implies high leverage. High leverage indicates a huge level of repayment that the company has to make in connection with the debt amount.
Through a wide variety of mobile applications.
UI/UX Design, Art Direction, A design is a plan or specification for art viverra maecenas accumsan.
Through a wide variety of mobile applications, we’ve developed a unique visual system and strategy that can be applied across the spectrum of available applications.
Most recent Debt/Equity Ratio greater than the median industry average: High debt/equity ratio implies high leverage. High leverage indicates a huge level of repayment that the company has to make in connection with the debt amount.
Through a wide variety of mobile applications, we’ve developed a unique visual system and strategy that can be applied across the spectrum of available applications.
A strategy is a general plan to achieve one or more long-term.
UI/UX Design, Art Direction, A design is a plan or specification for art.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commod viverra maecenas accumsan lacus vel facilisis. ut labore et dolore magna aliqua.


There are always some stocks, which illusively scale lofty heights in a given time period. However, the good show doesn’t last for these overblown toxic stocks as their current price is not justified by their fundamental strength.
Toxic companies are usually characterized by huge debt loads and are vulnerable to external shocks. Accurately identifying such bloated stocks and getting rid of them at the right time can protect your portfolio.
Overpricing of these toxic stocks can be attributed to either an irrational enthusiasm surrounding them or some serious fundamental drawbacks. If you own such bubble stocks for an inordinate period of time, you are bound to see a massive erosion of wealth.
However, if you can precisely spot such toxic stocks, you may gain by resorting to an investing strategy called short selling. This strategy allows one to sell a stock first and then buy it when the price falls.
While short selling excels in bear markets, it typically loses money in bull markets.
So, just like identifying stocks with growth potential, pinpointing toxic stocks and offloading them at the right time is crucial to guard one’s portfolio from big losses or make profits by short selling them. Heska Corporation HSKA, Tandem Diabetes Care, Inc. TNDM, Credit Suisse Group CS,Zalando SE ZLNDY and Las Vegas Sands LVS are a few such toxic stocks.Screening Criteria
Here is a winning strategy that will help you to identify overhyped toxic stocks:

Most recent Debt/Equity Ratio greater than the median industry average: High debt/equity ratio implies high leverage. High leverage indicates a huge level of repayment that the company has to make in connection with the debt amount.
Through a wide variety of mobile applications, we’ve developed a unique visual system and strategy that can be applied across the spectrum of available applications.
A strategy is a general plan to achieve one or more long-term.
UI/UX Design, Art Direction, A design is a plan or specification for art.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commod viverra maecenas accumsan lacus vel facilisis. ut labore et dolore magna aliqua.
There are always some stocks, which illusively scale lofty heights in a given time period. However, the good show doesn’t last for these overblown toxic stocks as their current price is not justified by their fundamental strength.
Toxic companies are usually characterized by huge debt loads and are vulnerable to external shocks. Accurately identifying such bloated stocks and getting rid of them at the right time can protect your portfolio.



Overpricing of these toxic stocks can be attributed to either an irrational enthusiasm surrounding them or some serious fundamental drawbacks. If you own such bubble stocks for an inordinate period of time, you are bound to see a massive erosion of wealth.
However, if you can precisely spot such toxic stocks, you may gain by resorting to an investing strategy called short selling. This strategy allows one to sell a stock first and then buy it when the price falls.
While short selling excels in bear markets, it typically loses money in bull markets.
So, just like identifying stocks with growth potential, pinpointing toxic stocks and offloading them at the right time is crucial to guard one’s portfolio from big losses or make profits by short selling them. Heska Corporation HSKA, Tandem Diabetes Care, Inc. TNDM, Credit Suisse Group CS,Zalando SE ZLNDY and Las Vegas Sands LVS are a few such toxic stocks.Screening Criteria
Here is a winning strategy that will help you to identify overhyped toxic stocks:

Most recent Debt/Equity Ratio greater than the median industry average: High debt/equity ratio implies high leverage. High leverage indicates a huge level of repayment that the company has to make in connection with the debt amount.
Through a wide variety of mobile applications, we’ve developed a unique visual system and strategy that can be applied across the spectrum of available applications.
A strategy is a general plan to achieve one or more long-term.
UI/UX Design, Art Direction, A design is a plan or specification for art.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commod viverra maecenas accumsan lacus vel facilisis. ut labore et dolore magna aliqua.
There are always some stocks, which illusively scale lofty heights in a given time period. However, the good show doesn’t last for these overblown toxic stocks as their current price is not justified by their fundamental strength.
Toxic companies are usually characterized by huge debt loads and are vulnerable to external shocks. Accurately identifying such bloated stocks and getting rid of them at the right time can protect your portfolio.



Overpricing of these toxic stocks can be attributed to either an irrational enthusiasm surrounding them or some serious fundamental drawbacks. If you own such bubble stocks for an inordinate period of time, you are bound to see a massive erosion of wealth.
However, if you can precisely spot such toxic stocks, you may gain by resorting to an investing strategy called short selling. This strategy allows one to sell a stock first and then buy it when the price falls.
While short selling excels in bear markets, it typically loses money in bull markets.
So, just like identifying stocks with growth potential, pinpointing toxic stocks and offloading them at the right time is crucial to guard one’s portfolio from big losses or make profits by short selling them. Heska Corporation HSKA, Tandem Diabetes Care, Inc. TNDM, Credit Suisse Group CS,Zalando SE ZLNDY and Las Vegas Sands LVS are a few such toxic stocks.Screening Criteria
Here is a winning strategy that will help you to identify overhyped toxic stocks:

Most recent Debt/Equity Ratio greater than the median industry average: High debt/equity ratio implies high leverage. High leverage indicates a huge level of repayment that the company has to make in connection with the debt amount.
















Foster and maintain relationships with key decision-makers within assigned accounts. Act as the primary point of contact for clients, addressing concerns and resolving issues in a timely manner. Ensure high levels of customer satisfaction and loyalty. Identify upselling and cross-selling opportunities within the existing client base. Meet or exceed monthly and annual sales quotas. Collaborate with the sales team to ensure seamless service delivery and product implementation. Track account metrics including sales, service issues, and customer feedback. Provide regular updates to the management regarding account health and opportunities. Use CRM tools to manage account details and track communication history. Coordinate with internal departments such as technical support, billing, and product teams to ensure customer requirements are met. Participate in team meetings and provide feedback on market trends, competition, and customer insights.
Managed and expanded client portfolios, consistently achieving monthly sales targets, and contributing to the team's annual sales goals. Coordinated with technical support, billing, and product teams to meet client needs, resulting in a 30% reduction in service-related complaints. Provided regular reports to management on account performance, identifying potential risks and opportunities. Participated in industry events and seminars to gather insights on market trends and competitive landscape, informing strategy development.
Partner with Account Executives to qualify prospects and learn additional sales tactics to win deals together. Made 70-80 outbound calls per day with the intent to qualify leads and build relationships. Report on weekly results, both qualitative and quantitative Update and maintain Salesforce and SalesLoft database with new notes and intel gathering from conversations. Leverage several sales enablement tools and processes to hit key metrics for performance (Salesforce.com and Salesloft) Effectively execute marketing campaigns to increase brand awareness. Identify target accounts with Account Executives and have strategic conversations. SAAS- Selling an Investment Management Software
Develop Strategic Relationships: Foster and maintain strong, lasting relationships with key decision-makers within assigned accounts, serving as the primary point of contact. Ensure Client Satisfaction: Swiftly address client concerns and resolve issues to ensure high levels of client satisfaction and loyalty through proactive service and engagement.Drive Sales and Revenue Growth: Identify, qualify, and generate new business opportunities through direct calling, email, and contact efforts, consistently meeting or exceeding sales quotas.Consultative Selling: Use consultative and relationship-building selling techniques to identify connectivity solutions, leveraging Cogent’s global network footprint, including data centers and colocation facilities.Account Strategy and Planning: Develop and execute strategic account plans, working closely with the sales team to ensure seamless service delivery and efficient product implementation for clients.
Collaborated with external partners to develop customer solutions. Utilized CRM systems extensively, focusing on design and engineering. Identified new sales opportunities through in-depth industry and business research. Advised on product suitability based on customer's technical requirements. Crafted comprehensive proposals and presentations tailored to client needs. Recognized as a top earner for consistently hitting and exceeding targets. Achieved 115% of the sales objective, translating to $9,500 monthly revenue. Surpassed sales quota by 18% throughout the 3-year tenure. Addressed a wide range of customer needs, spanning business, informational, technical, and educational aspects. Managed applications and offered expert consultation on software development to prospective clients. Formulated detailed responses to inquiries related to complex system software.
Researching and developing customer solutions with AT&T external partners, CRM systems, including design and engineering Researching customer business and industry to identify new sales opportunities. Advising customers on suitability of products based on technical needs, preparing proposals, presentations. Awarded Top Sales representative for 150% of Sales objective $12,000 monthly. Provide solutions to customer's business, information, technical and educational needs. Formulates responses to customer inquiries/questions concerning moderately complex system software. Manage applications and provides software development and consultation to prospective users. Continued to exceed sales objective, by outperforming quota by 20% during 4-year tenure.
Implement Software for new designs. Expo product consultant Record Inventory Create innovative ideas for better production. Customer Care Service calls
This is the best website I have ordered something from. I highly recommend.
This is the best website I have ordered something from. I highly recommend.
This is the best website I have ordered something from. I highly recommend.
This is the best website I have ordered something from. I highly recommend.
• Service Description: This package is ideal for organizations looking to address specific, immediate needs in telecom management or to kickstart their cybersecurity initiatives. Services include initial assessments, bi-weekly advisory meetings, and basic cybersecurity implementation strategies.
Payment Terms: An initial deposit followed by a balance payment upon completion.
Service Description: Suitable for clients needing comprehensive advice on managing ongoing telecom operations or enhancing their cybersecurity posture. This package offers more frequent engagements including weekly strategy meetings, ongoing risk assessments, policy development, and intermediate cybersecurity enhancements.
Payment Terms: Payments are spread over quarterly installments to ease financial planning.
Service Description: Designed for long-term engagements, this package provides extensive support in telecom and cybersecurity management. It includes continuous process improvements, advanced threat detection, incident response strategies, and regular compliance audits, along with tailored training sessions for the client’s staff.
Payment Terms: Option for bi-annual or monthly payments to accommodate budgeting requirements.
Additional Notes • Customization: Each package can be further tailored to meet specific client needs. Add-on services or modifications to the service roster are possible and can be negotiated separately.
Additional Costs: Expenses such as third-party services, travel, and special resources will be billed separately as incurred.
Early Termination: A fee may apply for early termination of the contract, with specifics to be detailed in the contractual agreement.

Introduction:
The rapid advancement of technology continues to reshape industries, redefine user experiences, and challenge traditional business models. This comprehensive guide explores how to navigate and adapt to these ongoing changes in the technology landscape to ensure sustainable success.
Strategies for Adapting to Technological Advancements:
Adapting to technological change is not just about adoption but understanding and strategically integrating new technologies into your operations.
Conclusion:
The advancing technology landscape offers immense opportunities for growth and innovation. By adopting these strategies, you can effectively navigate these changes, leveraging technology to enhance operational efficiency, drive business growth, and deliver superior

Introduction:
As cyber threats evolve with increasing sophistication, understanding and implementing advanced cybersecurity tactics becomes paramount for individuals and organizations alike. This detailed guide explores deeper layers of cybersecurity measures to ensure robust protection in a complex digital world.
In-Depth Cybersecurity Strategies:
Effective cybersecurity requires a comprehensive approach that goes beyond the basics. Here’s how you can fortify your digital defenses with advanced strategies:
Conclusion:
Advanced cybersecurity tactics are essential in safeguarding against sophisticated digital threats. By adopting these strat

Introduction:
Welcome to your essential guide on mastering sales strategies. Whether you’re a seasoned sales professional or just starting out, this article will provide you with the tools and insights necessary to excel in today’s competitive market.
Engaging and Effective Sales Strategies:
Sales strategies are the backbone of successful marketing and business growth. Understanding and implementing these strategies effectively can significantly enhance your sales performance and business outcomes.
Conclusion:
Mastering sales strategies requires a blend of knowledge, tactics, and continuous adaptation. By focusing on these key areas, you can enhance your sales performance and propel your business to new heights. Embrace these strategies to not only meet but exceed your sales goals.
Call to Action:
Ready to skyrocket your sales? Apply these strategies today and start seeing the difference in your performance!

As a seasoned consultant specializing in Cybersecurity, Telecommunications, Technology, Business Development, and Sales Strategy, I am currently open to new opportunities. Please feel free to connect with me directly and discuss potential collaborations.
Phone: 972-799-7317 Email: info@rashadmatthews.comAll rights reserved